Innovative Solution for Ensuring Secure Collaboration: Dynamic Data Discovery, Compliance, and Protection Software
Advanced Information Protection for Microsoft 365, SharePoint Server and File Sharing Applications
NC Protect from archTIS augments access and protection controls using the unique identity a file builds over time.”
Softlanding Ltd Silver Partner archTIS
It starts the moment a file is first saved, with its content, name, authorship and date stamps. Throughout its life cycle it gains additional transient context such as the file location or information repository and classification levels.
NC Protect: Elevating Data Security and Access Control
Revolutionize your Data Security and Access Control with NC Protect
In the realm of cybersecurity, even with zero-trust tools, traditional security measures fall short once access is granted, allowing users to freely share, copy, or download sensitive data. The threats posed by insider actions, which often go unnoticed for months, call for a shift from reactive to proactive strategies.
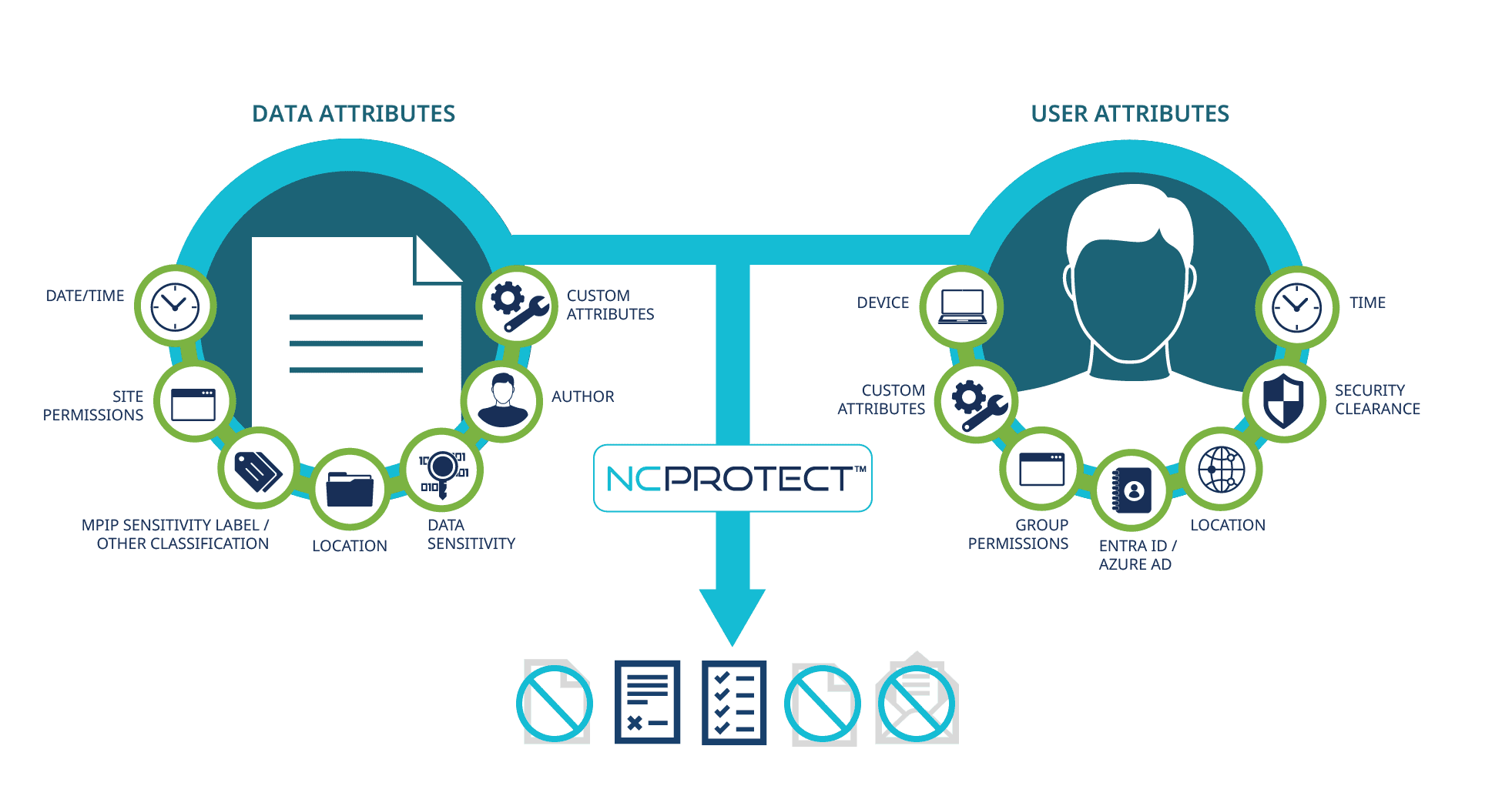
Enter NC Protect, the solution that redefines data-centric access control. By employing dynamic, attribute-based access control (ABAC), NC Protect safeguards against accidental and malicious data loss or misuse. It ensures that only authorized personnel access pertinent information in alignment with the principles of zero trust.
NC Protect excels by discovering, classifying, and securing unstructured data across various platforms, from files to chat content. Its real-time user context and file content comparison dynamically adjusts access and security, guaranteeing compliance with your business policies and regulations.
This cutting-edge solution seamlessly integrates into Microsoft 365 applications, encompassing SharePoint Online, OneDrive, Teams, Office, and Exchange, as well as on-premises systems like SharePoint Server and Windows File Shares. Additionally, it offers support for other cloud storage tools, including Nutanix Files.
Notable Recognitions:
- Finalist in the Microsoft Security Excellence Awards for Compliance & Privacy Trailblazer
- Cybersecurity Excellence Gold Award 2022
- CyberSecurity Breakthrough Awards 2022 Policy Management Solution of the Year
Empowering Data Protection:
Discover, Classify, and Secure Data:
Effortlessly locate and classify sensitive data in diverse environments, adhering to consistent rules. Monitor access to sensitive data for compliance purposes.
Proactive Prevention: Stay ahead of data loss, misuse, and human errors. Dynamic security adaptations adjust access, usage, and sharing privileges based on real-time user context and file content.
Secure Collaboration: NC Protect facilitates secure collaboration by intelligently adapting access and security in accordance with user and file context. This ensures compliance with organizational policies and regulations.
Key Features:
-
Automated sensitive content discovery and classification based on content sensitivity
-
Customizable protection based on user and file attributes, governing access, copying, and sharing
-
Dynamic adjustments to access and protection policies as files move across users and locations
-
Secure read-only viewing via a built-in Secure Reader
-
On-demand file encryption
-
Redaction of sensitive keywords or phrases
-
Obfuscation/hiding of files from unauthorized users
-
Contextual ribbon rule restrictions in Microsoft Office apps
-
Addition of security watermarks to documents
-
File integrity checks to prevent malicious overwriting
archTIS is a member of Microsoft Intelligent Security Association
Supported Platforms:
- Microsoft 365 Suite: SharePoint Online, OneDrive, Office, Exchange
- Microsoft Teams: Conditional Access and Protection for Teams Chat and Files
- Microsoft Office 365: File encryption and access restriction
- SharePoint Server On-Premises: Discovery, Protection & Auditing for Cloud Collaboration
- Windows File Shares: Discovery, Protection & Auditing for File Shares
- Nutanix Files: Discovery, Protection & Auditing for Nutanix Files
Experience the Future of Data Security: Request a Demo
Unlock the potential of NC Protect and witness its ABAC-powered zero trust data security in action. Request a demo today and discover secure collaboration across Microsoft 365, SharePoint Server, Windows File Shares, and Nutanix Files.
Request a Demo

